- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Accessing Audit Log Information from the Reporting Server via Splunk API
Accessing Audit Log Information from the Reporting Server via Splunk API
In NIOS 8.3, you can use the Splunk API to retrieve reporting data from the Infoblox reporting server. From any scripting language like Perl or Python, a user can access DDI data gathered from Infoblox members on the reporting server.
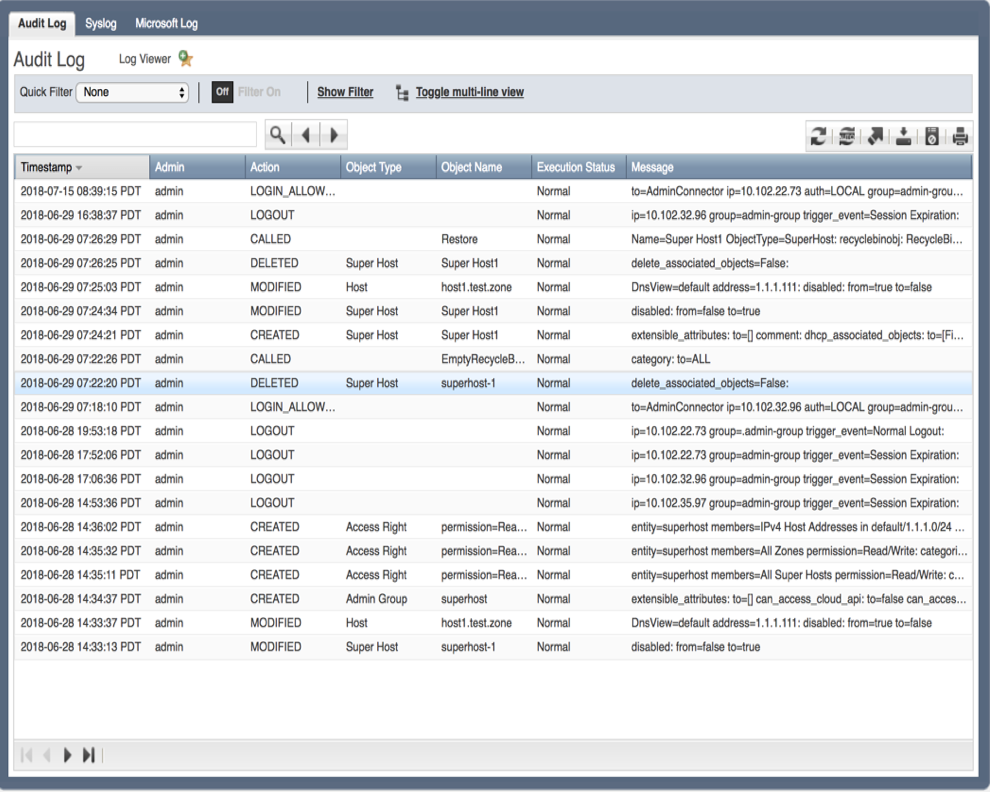
Let us consider a typical use case for network operations of an enterprise or a service provider network. You need to audit the work that a user had done on the Infoblox Grid. You could go to the Audit Log and do either a direct search on the UI or download the entire audit log as a CSV file and then search within the CSV file. Also, you could view the Audit Log Events report.
This method works perfectly well if you do this on an occasional basis. What if you needed to do this frequently? It can become very time consuming, and we need to find an efficient solution.
Fortunately, with Splunk API, you can automate the task.
As of NIOS 8.3, you can make REST API calls to the Infoblox Reporting Server to access audit log information as well as DDI information. The audit log information can then be ingested into the auditing applications for processing.
Prerequisites
- You must know Splunk, Splunk API, and Postman.
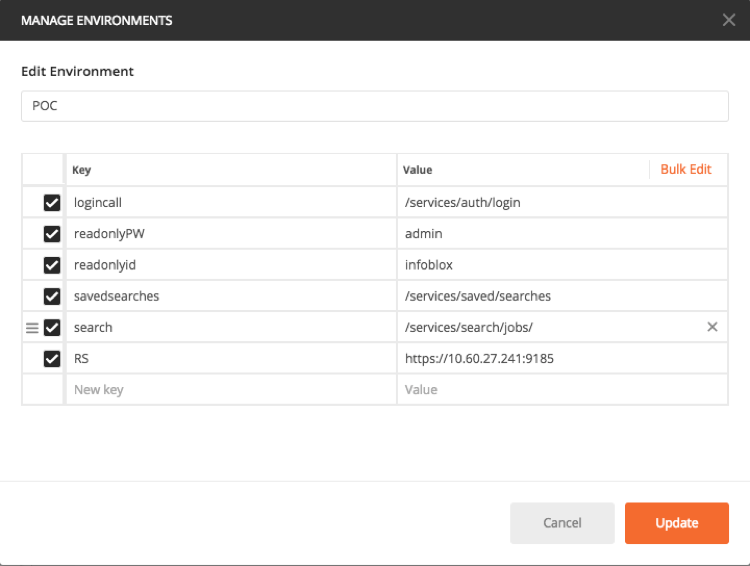
- For example, we will use Postman (www.getpostman.com) to prototype the API calls. Access the sample JSON code and environment variables and import it into Postman.
- After importing the JSON code and environment variables, modify the RS environment variable with the IP address of your reporting server. Ensure the port number is 9185. Click Update.
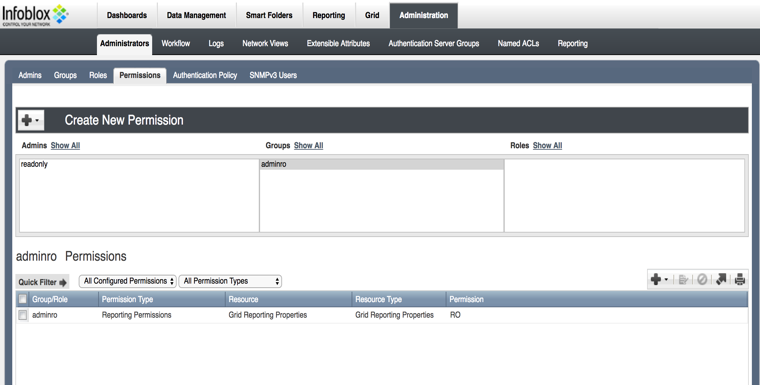
Log in as a user with administrative privileges into the Infoblox GUI. Create a user and user group with readonly credentials. Ensure the permissions are set similar to the screenshot below.
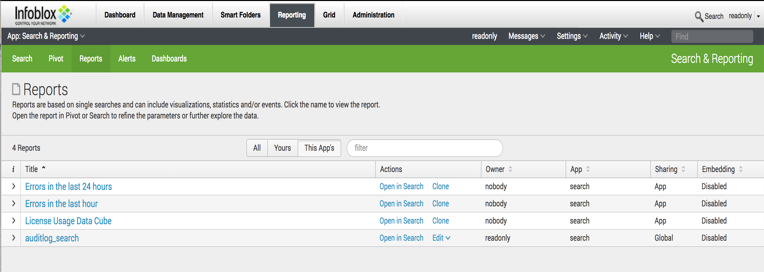
Logout as the administrator and log in as the readonly user and go to the reporting section.
Example
For this example, we will use Postman for demonstrating the API calls.
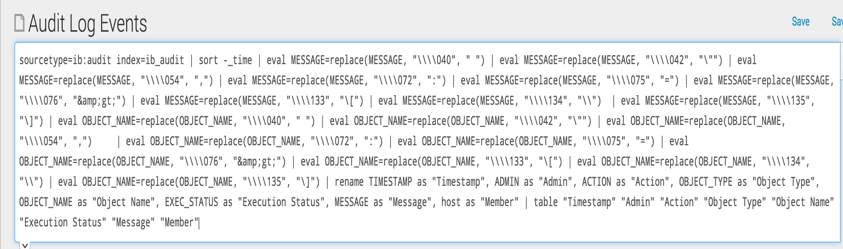
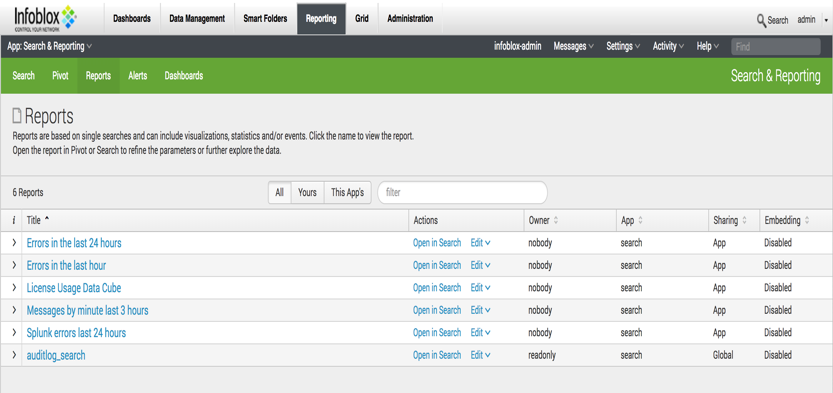
To jumpstart the search on audit log information, we are going to get search code from the Audit Log Events report on the Infoblox Reporting Server. Ensure the App in the left-hand corner of the screen is set to Infoblox Reporting and Analytics. Navigate to Reporting à Audit Log Events.
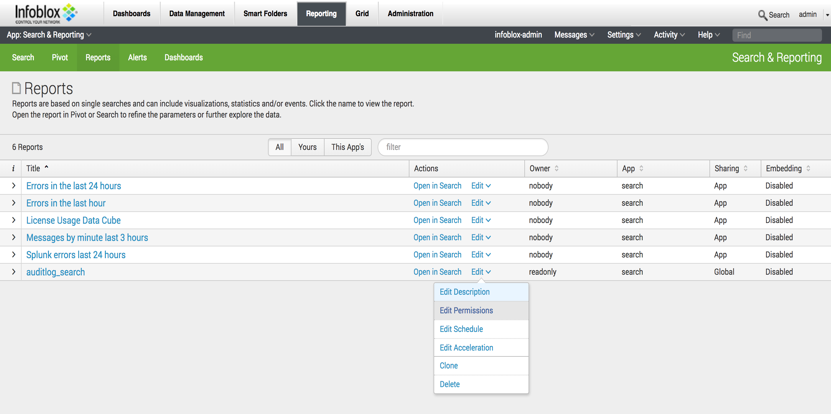
Click on Open in Search to get search code. Highlight and copy the search code to a clipboard.
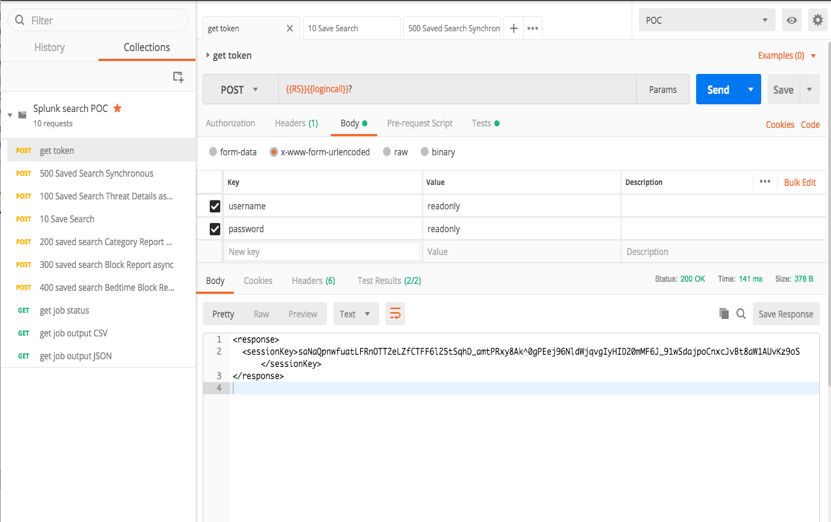
On Postman, use the ‘get token’ request to get a token/session ID from the reporting server. Change the username and password to the read-only username created in the prerequisites. Click Save and then Send. You should see a session key like the example below.
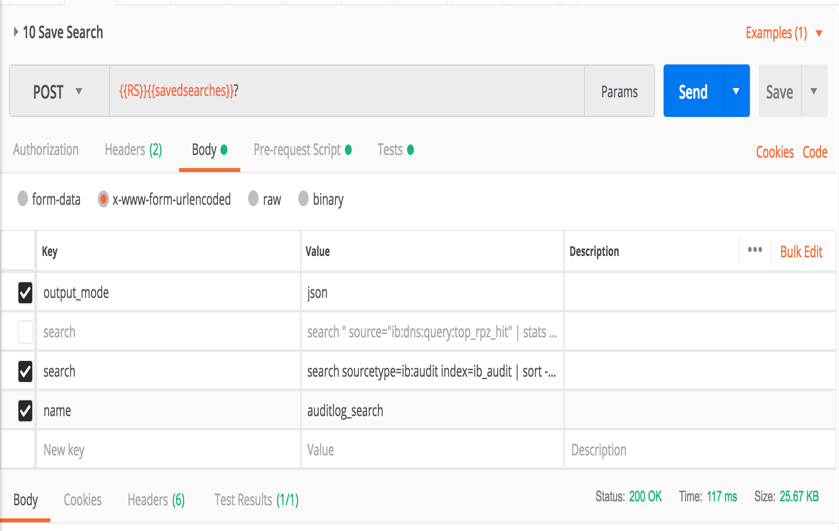
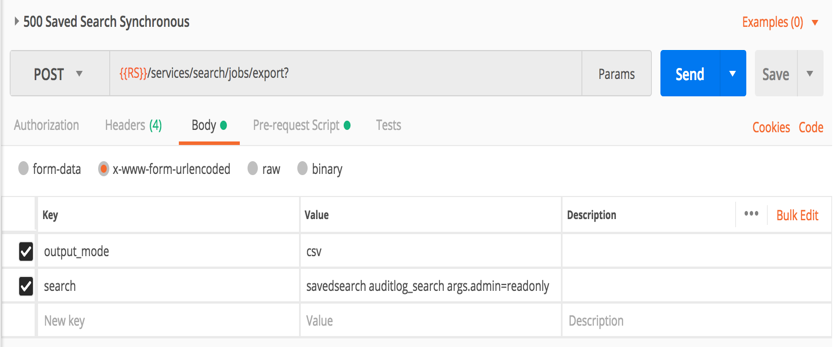
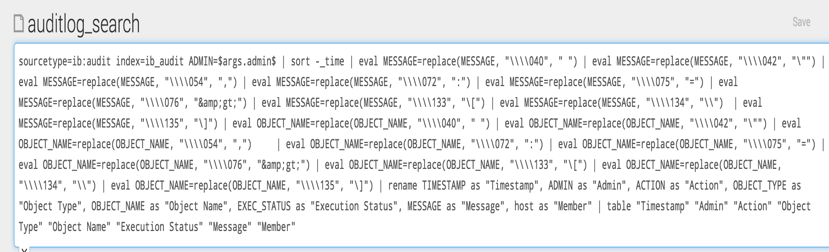
Paste the search code in the Save Search request after the ‘search sourcetype =’ string and then save it. Click on the Send button.
This search is sent to the reporting server to create a search/report called auditlog_search.
After creating this search, you will need to edit permissions to make it accessible to other users because this search was created by the user read-only.
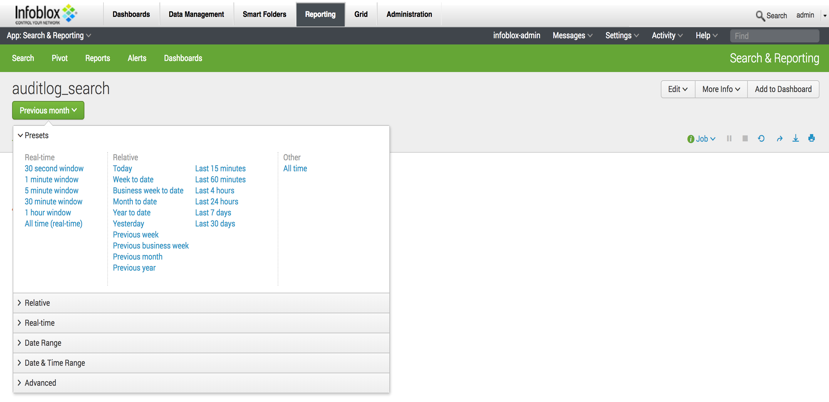
Lastly, you will need to set the time window for your search.
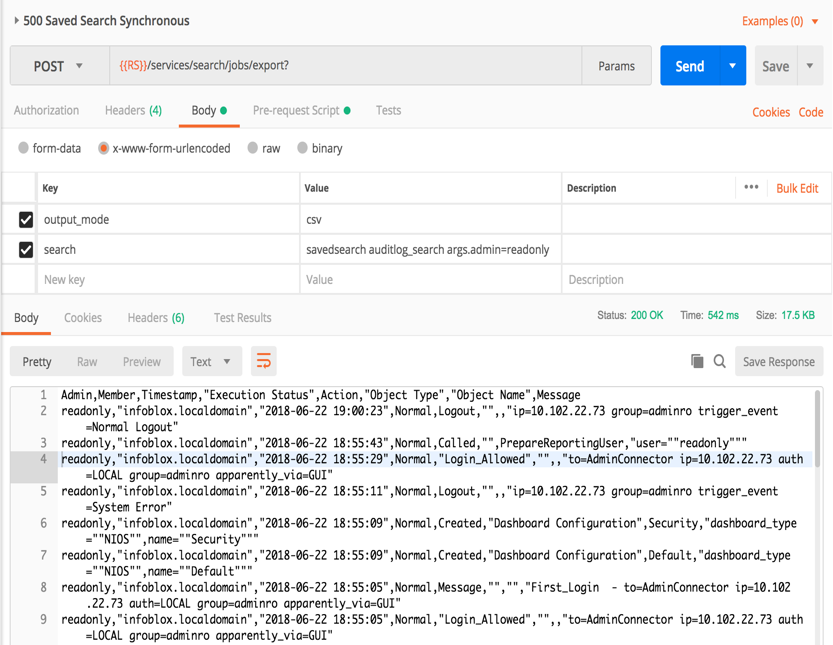
On Postman, now that we have created search called auditlog_search on the Infoblox Reporting Server, use the Saved Search Synchronous request. A variable will be used to pass the username that will be searched. The variable is called args.admin.
On the Infoblox Reporting server, here is the Splunk search string with the variable encased in $. ADMIN is a variable in this search code. This was added into the search code.
Now we can run the API call from Postman and get the following output.
This data above shows the readonly username performing various functions. If you were trying to troubleshoot an issue, you could determine if this user may have been the cause of the misconfiguration. If you wish to view another user, then change the args.admin variable to another user.
Conclusion
This document demonstrates how you can use the REST API interface to access information from the Infoblox Reporting Server. The REST API calls can be incorporated into the PERL scripts, Python scripts or other applications to obtain the information on a frequent basis.
Reference
- https://docs.infoblox.com/display/nios83/Reporting+Data+Model – documents the Splunk variables and datatypes that are unique to the Infoblox Reporting Server.
- http://docs.splunk.com/Documentation/Splunk/7.1.2/RESTREF/RESTprolog - documents the Splunk API.
- getpostman.com – website for Postman.