- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Infoblox and Carbon Black integration overview and demo videos
Hi there,
With this post I'm going to make a technical overview of the integration between Infoblox DDI and Carbon Black Response (named Carbon Black/Bit9 early) which was done in 2015. A solution note for the integration is posted here.
The integration requires an additional connector installed on Carbon Black Response server, local RPZ zone(s) or ActiveTrust feeds on Infoblox DDI side and configure the connector as an external syslog server for RPZ events.
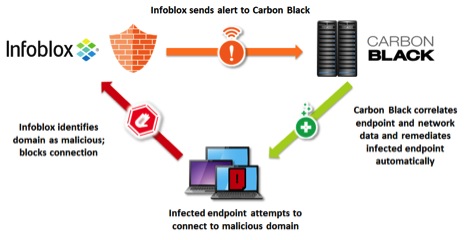
The Carbon Black Infoblox Secure DNS connector ingests reports (RPZ hit events) from the Infoblox Secure DNS appliance and correlates them against data in the connected Carbon Black Response server. The connector can then take one or more actions based on these reports, including killing the offending process from the endpoint, isolating the system from the network, and creating an alert for future followup.
Infoblox RPZ syslog messages are sent to the connector, which can either run on its own host or on the Carbon Black server itself. The connector then correlates the DNS information with Carbon Black to determine what process caused the DNS lookup. This correlation can only occur if the endpoint has attempted to establish a TCP or UDP connection with another host. A Carbon Black network connection event is only generated when a TCP SYN or UDP packet is sent to a target host, and these network connection events are used to correlate the DNS request against the Carbon Black Response data.
Because of this limitation RPZ zones/feeds or RPZ rules should be configured to redirect endhosts to a walled garden site/blackhole/honeypot. In other words if RPZ returns NXDOMAIN (default action for the ActiveTrust feeds) or NODATA, Carbon Black does not receive a netconn event and this connector cannot correlate the activity against a running process on the endpoint. The IP does not have to correspond to a real host; a network connection event will be generated as long as the host attempts to contact the target IP, even if it doesn't exist or is unreachable.
This also means that DNS Data Exfiltration/Infiltration/Tunneling can be stopped on Infoblox DNS but Carbon Black Response can not correlate the DNS information with a process because no TCP SYN or UDP packet is send to a remote host.
The detailed step by step guide is available on the connector's github page.
The following videos demonstrate the integration.
BR,
Vadim