- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Active Directory Dynamic Updates aren't working
[ Edited ]- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 06:48 PM - edited 03-20-2021 05:22 PM
I thought I followed to a "T" the directions in this thread to setup dynamic updates for a Windows AD environment:
Active Directory Integration - Infoblox Experts Community
However, my Windows servers are still logging DDNS errors about being unable to update their records. I did also implement GSS-TSIG.
I thought I double checked all the settings, but still no dice. I do see in the logs this error:
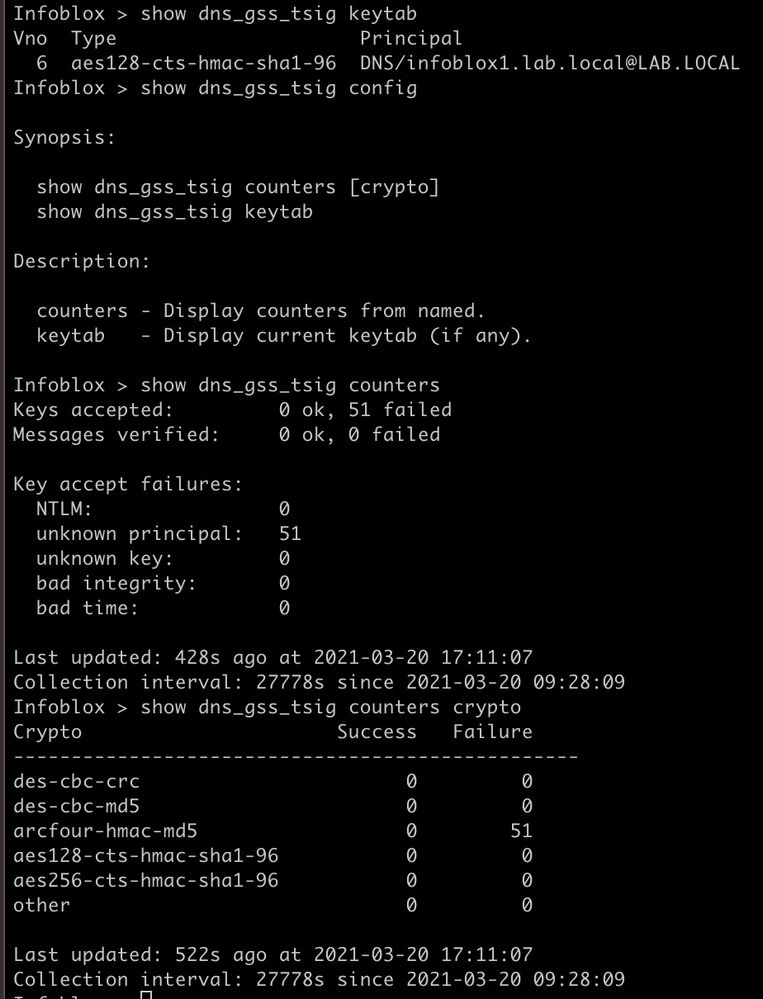
172.26.13.249#64849: GSS-TSIG authentication failed for (DNS/infoblox1.lab.local@LAB.LOCAL, kvno 3, arcfour-hmac-md5): unknown principal
172.26.13.249 is the client trying to do the update. Infoblox1 is of course the DNS server the updates should be going to. What is baffling me is the 'unknown prinicpal'. I know that's a Kerberos thing, but I don't know how to fix it.
Here's how I got the keytab file:
ktpass -princ DNS/infoblox1.lab.local@LAB.LOCAL -mapuser svc-infoblox -pass password -out ktpass1.keytab -ptype krb5_nt_principal -crypto AES128-SHA1
Targeting domain controller: ADDC01.lab.local
Using legacy password setting method
Successfully mapped DNS/infoblox1.lab.local to svc-infoblox.
Key created.
Output keytab to ktpass1.keytab:
Keytab version: 0x502
keysize 68 DNS/infoblox1.lab.local@LAB.LOCAL ptype 1 (KRB5_NT_PRINCIPAL) vno 6 etype 0x11 (AES128-SHA1) keylength 16 (0x0cf8a9305bd887b4b0c5d98468673157)
-------
I should also add that I went into ADSI edit on my domain controller, looked up the service account object, and reviewed the SPNs. I see:
DNS/infoblox1.lab.local
DNS/svc-infoblox
And the SPN is also listed via the CLI:
setspn -L svc-infoblox
Registered ServicePrincipalNames for CN=svc-infoblox,OU=Service Accounts,DC=lab,DC=local:
DNS/infoblox1.lab.local
DNS/svc-infoblox
-----------
From the NIOS syslog log:
2021-03-20T16:11:14-07:00 daemon infoblox1.lab.local named[29262]: err client @0x7ff33c4c6570 172.26.13.249#61761: update 'lab.local/IN' denied
2021-03-20T16:11:14-07:00 daemon infoblox1.lab.local named[29262]: err 172.26.13.249#59772: GSS-TSIG authentication failed for (DNS/infoblox1.lab.local@LAB.LOCAL, kvno 6, arcfour-hmac-md5): unknown principal
2021-03-20T16:11:14-07:00 daemon infoblox1.lab.local named[29262]: err gss_accept_sec_context: continuation call to routine required
2021-03-20T16:11:14-07:00 daemon infoblox1.lab.local named[29262]: err client @0x7ff33c4c6570 172.26.13.249#64041: update 'lab.local/IN' denied
2021-03-20T16:11:14-07:00 daemon infoblox1.lab.local named[29262]: err 172.26.13.249#56005: GSS-TSIG authentication failed for (DNS/infoblox1.lab.local@LAB.LOCAL, kvno 6, arcfour-hmac-md5): unknown principal
2021-03-20T16:11:14-07:00 daemon infoblox1.lab.local named[29262]: err gss_accept_sec_context: continuation call to routine required
Re: Active Directory Dynamic Updates aren't working
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2021 08:31 AM
I should also add that I installed the MIT kerberos package on a domain controller, which gives me the 'kinit' command which can test keytab files. I ran:
kinit -V -k -t mykeytab.keytab DNS/infoblox1.lab.local@LAB.LOCAL
And it can successfully authenticiate via kerberos 5. So from as far as I can tell, everything from the AD side is there and works. And I have a valid keytab file.
Re: Active Directory Dynamic Updates aren't working
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 03:37 PM
Initial quick thought is -mapuser svc-infoblox should be -mapuser svc-infoblox@lab.local
Re: Active Directory Dynamic Updates aren't working
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 04:03 PM
yes, you are right. It was either a copy/paste or typo in my OP that omitted that. The current ktpass command I'm using is:
ktpass -out dns.keytab -mapuser svc-infoblox@LAB.LOCAL -Pass password -mapop set -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -princ DNS/infoblox1.lab.local@LAB.LOCAL
That resulting keytab file works with kinit. Through some trial and error I now have a different syslog failure:
172.26.13.249#62141: GSS-TSIG authentication failed for (DNS/infoblox1.lab.local@LAB.LOCAL, kvno 17, aes256-cts-hmac-sha1-96): key not found
So still broken but a different error.
Re: Active Directory Dynamic Updates aren't working
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2021 03:55 PM
Here is link to a good guide which should satisfy your needs.
Pay Attention at your crypto settings when using ktpass.
>ktpass -princ DNS/FQDN_instance@REALM -mapuser AD_username -pass password -
>out filename.keytab -ptype krb5_nt_principal -crypto encryption all
With this, you generate all possible keys with different crypto at once
>DNS/infoblox1.lab.local@LAB.LOCAL, kvno 17, aes256-cts-hmac-sha1-96): key not found
You should upload and assign the generated the key with aes256-cts-hmac-sha1-96 crypto